
By Adam Carter
It’s almost two years since I started investigating Guccifer 2.0.
Since then, largely thanks to several other independent researchers and their contributions, much has been discovered. The purpose of this article is to go back over all of the discoveries made during the last two years, as well as the various challenges received, and to provide an up-to-date status on the validity of different areas of research into Guccifer 2.0. The articles and findings at issue are as follows:
- Guccifer 2.0’s First Documents
- NGP-VAN Archive Study
- CF.7z Archive Study
- Language Analysis
- Blogging & Social Media Activity
- Potential Ties To DCLeaks
- E-Mail Suggesting Operations In Us Time Zone
- Loaded For Guccifer – UCT +3
- West Coast Fingerprints
- Impact Of Documents Released
- Guccifer 2.0’s Russian Fingerprints
- Determination To Attribute Self To WikiLeaks, DCLeaks, etc.
- CrowdStrike’s Absence Of Evidence
- Mueller’s Indictment
- GRU Frames Russia & Manufactures Evidence To Support CrowdStrike?
Guccifer 2.0’s First Documents

The files that Guccifer 2.0 initially pushed to reporters appear to have been constructed through a process that involved them being deliberately tainted with Russian metadata, a Russian stylesheet entry and in some cases embedded Russian error messages.
While this writer was incorrect in my earliest reasoning on the presence of Flood’s name, we can now fully account for it with 100% certainty. Additionally, conclusions regarding deliberate Russification of Guccifer 2.0’s documents have been reinforced thanks to the Forensicator’s consideration of the error messages therein.
If anyone has tangibly debunked anything this author has claimed in any significant way, it’s the Forensicator who has done so, thanks to the above. Forensicator was even kind enough to give me the opportunity to figure out which of the two shortlisted documents was the original source so I could contribute something towards it.
In other words, this author has not simply run with any single narrative based on a first-glance take, or from a political standpoint. Instead, I and others have actively worked to report on the truth of the matter as factually as possible, updating my understanding as additional material comes to light.
NGP-VAN Study

Approximately fifteen months ago, the Forensicator published a study of an archive Guccifer 2.0 had released in September 2016, which contained a collection of old files mostly related to NGP-VAN, voters, and donors. Key findings included the revelation that the earliest transfers recorded were in July 2016, that a USB device had been used to transfer files and that a number of archives were moved to a USB device (or archived directly to it) on September 1, 2016, before being archived again in another format prior to publication on September 13, 2016.
Due to the difference in timestamp storage conventions between the different archive formats, Forensicator found that the archives compiled in September were, according to the evidence available, most likely to have been compiled where Eastern (EDT) time zone settings were in effect.
That study has been the subject of some controversy, although the controversy that exists is mostly built on conflating the findings with various interpretations of them, and with reporting on the study conducted by third parties. We’ve seen a few journalists misconstruing one of Forensicator’s conclusions as being some sort of bandwidth challenge when the reality is that the major conclusion relates to how the speeds observed in testing managed to fit well with USB transfers (which reinforced other indicators of USB usage such as identifying files being stored on a FAT-32 file system).
Again: Whether people could or couldn’t obtain the speeds observed via Internet transfer is really an argument against a comment made in passing by Forensicator about it being improbable to obtain those speeds for the files that were analyzed under the circumstances Guccifer 2.0 was thought to be operating in (i.e., a foreign hacker remotely hacking the DNC).
However, this was not the point actually being made in the respective conclusion in Forensicator’s study, as the original study shows and the Forensicator’s follow-up article clarified. This is also an argument this writer addressed in an article published last year, titled “Distortions and Missing The Point.”
Since the publication of Forensicator’s initial analysis, we’ve also seen a journalist from TechDirt attempt to argue that there was some sort of “conversion error” and suggested that expressing transfer rates in MB/s rather than Mbps somehow delegitimizes something or someone. It was silly, and their readers were calling out the nonsense in comments before I’d even considered writing a rebuttal.
By the end of July 2018, as part of a hit-piece against myself and associates, Duncan Campbell presented an argument against Forensicator’s study based on speculation, manipulation of Forensicator’s report, and the misconstruing of statements from former NSA Technical Director, Bill Binney. Putting Campbell’s smears and debunked conspiracy theory aside, we’re left with two primary objections to the meat of Campbell’s allegations:
- WinRar and 7-zip were chosen deliberately in order to leave a false EDT time zone breadcrumb to fool digital forensics investigators.
- The July 5th transfer date was arbitrarily set for the purpose of the NGP-VAN release in to deceive people into thinking Guccifer 2.0 had something to do with Seth Rich (the DNC staffer murdered five days after that date).
However, there’s no evidence suggesting timestamps were manipulated in the way that was suggested (it’s an entirely speculative theory, and the NGP-VAN archive isn’t the only place we’ve seen the July 5th date).
Whether Guccifer 2.0 did or didn’t deliberately try to leave an EDT time zone breadcrumb by choosing archiving applications specifically for that purpose is, again, difficult to prove but it seems quite an obscure place to try to leave a false trail – especially just to leave evidence that contradicts what Guccifer 2.0 claimed about himself. Certainly, one can argue that the evidence may have been cooked up just to fool digital forensic investigations: it’s a possibility, for sure, but that conclusion is not supported by evidence, and there’s nothing in such arguments that can be tested.
Of course, as this article hopefully makes clear, you could completely disregard the NGP-VAN archive study if you wanted to, but you would still be left with a plethora of evidence that suggests Guccifer 2.0 operated from within in the United States.
Duncan further claimed that Bill Binney had changed his mind and was running in the opposite direction since Binney had clarified that we cannot be sure that the transfers scrutinized were necessarily a transfer from the DNC. In the real world, this is a position Forensicator has long held and provided clarification on back in August 2017 so trying to frame this as some sort of defection, disagreement or division is simply deceitful.
CF.7z Archive
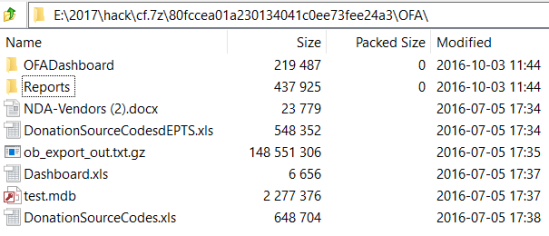
In September 2017, Stephen McIntyre analyzed the “cf.7z” archive that Guccifer 2.0 had released on October 4, 2016, and discovered indication of US central time zone. Forensicator followed this up with additional observations, pointing out how files in the cf.7z archive filled in gaps that were identified in the NGP-VAN archive.
In October 2017, McIntyre published an article titled “Guccifer 2: From January to May 2016,” which made a case for Guccifer 2.0 genuinely hacking to access files that appear in that archive. McIntyre stated:
“To my eye, there is convincing evidence that G2 actually hacked Democrat Party computers from at least January 2016 on,” noting that the dates of transfers would have been in the timeframe that APT29/Cozy Bear were thought to have infiltrated the DNC.
McIntyre also observed very low transfer rates and noted that this is far more in line with what is expected from hackers when transferring files. Of course, dates going back that far could also occur if files were archived directly from a mounted image (e.g., such as those made of DNC servers by CrowdStrike). ThreatConnect did highlight the implausibility of Guccifer 2.0’s claims concerning using NGP-VAN as a vector, but this doesn’t mean I disagree with McIntyre’s assessment.
Based on the CF.7z file, I agree that it does seem, from transfer dates, rates, and other factors, that Guccifer 2.0 could have hacked and/or had access to files before June. It’s what the evidence suggests more strongly in the case of this particular archive.
Language Study

In 2016, Professor Michael J. Connolly was cited by Vice/Motherboard’s Lorenzo Franceschi-Bicchirai, stating that Guccifer 2.0 seemed to lack traits that would suggest he was Russian. Connolly was the only language expert willing to be named in all of the reporting I could find, so this author sought to understand what traits he may have been referring to.
After reading several articles, it seemed clear that key difficulties for Russians communicating in English include: definite and indefinite articles, the use of presuppositions and correct usage of say/tell and said/told. Throughout 2017, I constructed a corpus of Guccifer 2.0’s communications and analyzed the frequency of different types of mistakes. The results of this work corroborate Professor Connolly’s assessment.
Overall, it appears Guccifer 2.0 could communicate in English quite well but chose to use inconsistently broken English at times in order to give the impression that it wasn’t his primary language. The manner in which Guccifer 2.0’s English was broken, did not follow the typical errors one would expect if Guccifer 2.0’s first language was Russian.
To date, Connolly’s language study has not drawn any significant objections or criticism.
Blogging & Social Media Activity

In September 2017, this writer collected and analyzed data relating to Guccifer 2.0’s social media and blogging activity, finding that both appeared to fit in with what would be expected if Guccifer 2.0 was operating within the US Central time zone. While it is possible the persona could have done this deliberately, it wouldn’t make much sense for the Guccifer 2.0 persona to claim to be Romanian, while tweeting and blogging at times that would suggest they were in US time zones. Perhaps Guccifer 2.0 wanted to catch Americans at times of peak activity?! (This wouldn’t explain the dip in activity at lunchtime being there too, though!)
While these activity levels were independently recorded and suggest a US origin for Guccifer 2.0 (which corroborates other indications found), it is, of course, just circumstantial and people can dismiss this on the basis of the arguments mentioned above.
Another discovery made as part of this was the fact Guccifer 2.0 engaged in very little activity on Saturdays. This observation comes simply from the evidence of the persona’s activity, as charted below.

Potential Ties To DCLeaks

DCLeaks appeared in June 2016, publishing various leaks from political figures. Among the numerous files published, they released emails of William Rinehart as well as some files relating to the DNC that would later show up as attachments on John Podesta’s emails. Stephen McIntyre noted that the phishing emails for Podesta and Rinehart also shared identical syntax and that this may indicate DCLeaks sources were connected to the phishing efforts.
Shortly after he emerged, Guccifer 2.0 pushed batches of emails from a few DNC-connected individuals such as Sarah Hamilton to DCLeaks.
Some in the press and the cybersecurity industry have speculated that Guccifer 2.0 could have been connected to DCLeaks management. I have tried to quantify the degree of association demonstrated and found nothing to show he was any more than a source for DCLeaks with access to an area to upload his content.
The overlap of activities and Podesta attachments does serve as circumstantial evidence that could indicate there was more to the relationship. That said, the only things I have found substantiating any closer association between the two was an apparent hoax in 2016, followed by another occurring earlier this year.
At this time, there is no definitive evidence that substantiates or discounts a possible relationship between Guccifer 2.0 and DC Leaks.
E-Mail Suggesting Operations In Us Time Zone

In September 2017, Stephen McIntyre posted an article on his site regarding an email communication made by Guccifer 2.0 in which it seems to reveal Guccifer 2.0’s local time zone being set to US central time. This also fell in line with what Stephen McIntyre identified in an analysis of the “cf.7z” archive, in addition to the social media activity analysis detailed in the previous section above.
Again, this was independently recorded and suggest a US origin for Guccifer 2.0. To date, there has been no counter to McIntyre’s finding.
Loaded For Guccifer – GMT +3 Time Zone Indications

At the beginning of 2018, David Jonathan Blake created a blog called Loaded For Guccifer, looking at various pieces of evidence relating to Guccifer 2.0 (as well as DCLeaks and other similar topics).
One of his articles, titled “Doc 1: Part 3 … Back to Romania!” looks at datastores embedded within Guccifer 2.0’s files and reveals that there are indications of GMT +3 time zone present in some of Guccifer 2.0’s first documents as a result of these being present. However, the Forensicator would soon challenge the assumption that this serves as evidence for a Romanian Guccifer 2.0
West Coast Fingerprints & Tracking Changes

In May 2018, Forensicator published a report titled “Guccifer 2’s West Coast Fingerprint,” detailing a discovery revealing that one of the files that had the +3/+4 timestamps embedded in the manner revealed by Blake’s research had been saved on a machine that had PDT time zone settings in effect, which was revealed as tracking changes had been left on for that document). This raises the prospect that the +3/+4 timestamps inferred from the datastore objects may have been deliberate.
Impact of Documents Released – Cui Bono?

It is a severely under-appreciated point that, despite having access to John Podesta’s attachments and other documents (and releasing thousands of files), Guccifer 2.0 somehow managed to avoid releasing anything that was damaging to the reputations of Podesta, Hillary Clinton or the Democratic party’s leadership. None of the material Guccifer 2.0 published had a negative impact on Clinton’s campaign, (though the persona’s access to documents suggests its operator would have had the capability to do so). Even the documents given to Aaron Nevins made zero impact on the General Election in relevant states.
On the other hand, Guccifer 2.0 did manage to very effectively smear the public perception of the DNC leaks and Podesta emails as published by WikiLeaks, and to generate headlines expressing outrage that funneled attention away from their contents. Without arguing attribution at all, one could draw the conclusion the party which most benefitted from the actions of Guccifer 2.0 – even a Russian Guccifer 2.0 – was, in fact, the Hillary Clinton campaign.
Guccifer 2.0’s Russian Fingerprints

At the end of November 2018, Forensicator published a report titled “Guccifer 2.0’s Russian Breadcrumbs,” covering all of the individual files that Guccifer 2.0 published via his blog, which exhaustively detailed the various breadcrumbs left behind by Guccifer 2.0.
As part of the report, Forensicator presented the following metadata mosaic, showing the many unnecessary edits carried out by Guccifer 2.0 and that in most batches of modified documents Russian breadcrumbs of some sort were being left behind.

source: https://theforensicator.wordpress.com/guccifer-2s-russian-breadcrumbs/
The report covers document tweaking times versus independently recorded activity (e.g., social media and blogging activity times, previously discussed above), sources of documents (in terms of where else they appeared), attribution of documents to their relevant organizations and various other anomalies in evidence that seem to contradict the Russian attribution.
The analysis comes with a new revelation of activity on the East coast of the US, from a file that was edited and published on July 6, 2016 (one day after the July 5 transfer date observed in the NGP-VAN archive study).
To quote a follow-up article Forensicator published on this topic (titled “Guccifer 2 Returns To The East Coast“):
Now, we have this additional East Coast indication, which appears just one day after the ngpvan.7z files were collected. This new East Coast indication is found in a completely different group of files that Guccifer 2 published on his blog site. Further, this East Coast finding has its own unique and equally unlikely method of derivation.
Determination To Attribute Self To WikiLeaks, DCLeaks, etc.
From the day he emerged, Guccifer 2.0 was keen to attribute himself to the alleged DNC hack and attribute himself to WikiLeaks. Although he had claimed on day one that he’d sent files to WikiLeaks, the first time Guccifer 2.0 sent anything was in July (based on Mueller’s indictment).
Guccifer 2.0 also made a false claim about DCLeaks (and possibly not the only one), stating it was a sub-project of WikiLeaks. It is evident, then, that Guccifer 2.0 wanted to be perceived as having ties to DCLeaks management.
In addition to this, Guccifer 2.0 tried to attribute himself to Seth Rich on August 25, 2016, in a Twitter DM conversation he had with actress Robbin Young.
What’s interesting about this is that on August 9, 2016, WikiLeaks offered a $20,000 reward for information leading to the arrest of Rich’s murderer. On August 25, 2016, Assange was due to be interviewed by Fox News and by then many had got their hopes up about Assange and were hoping that he would reveal the source of the DNC leaks (under the assumption that Rich was involved and that his death would make it somehow permissible for WikiLeaks to divulge such information).
An important question: Was the Guccifer 2.0 persona trying to “poison the well” by attributing himself to Rich just in case it did turn out there was any substance to rumors)? Or was he just trying to prop up a conspiracy theory and throw people off the Russian trail?
Interpretations of these acts vary considerably depending on the source, but the first of these hypotheses is more coherent with what other evidence in the public domain has revealed about Guccifer 2.0’s efforts and apparent objectives.
CrowdStrike & Coincidence

Around March 26, 2016, approximately five days after John Podesta’s email was phished, CrowdStrike coincidentally started working with the DNC on investigating the NGP-VAN breach that had occurred three months earlier, an arrangement that would persist for five weeks.
It appears that the first mention of the purpose of this visit was made retroactively, at the very end of those five weeks. Guccifer 2.0’s first follower and the first piece of APT-28 malware was constructed just prior to the end of those five weeks.

As soon as they had finished that investigation, Crowdstrike was called back in to investigate a breach. CrowdStrike subsequently visited the DNC around May 5, 2016. Coincidentally, this was the same day on which the second piece of APT-28 malware was compiled.
Crowdstrike then installed Falcon across the network and judging on FEC records, CrowdStrike remained active at the DNC for about 5-6 days, until around the 10th/11th. As it happens, the third piece of APT-28 malware was compiled on May 10, 2016.
Between May 19-25, 2016, a number of DNC emails were acquired (it seems most likely from an internal SMTP server). According to statements retroactively made by CrowdStrike long after the event, they didn’t have Falcon running as per the product’s advertisements at the time (i.e., designed to keep hackers out) and were just “monitoring.”
The company never published incident specific evidence (e.g., logs showing how/when emails were acquired). Half the malware that they published IOCs for was compiled while CrowdStrike were working at/with the DNC.
Additionally, within two days of Assange announcing that WikiLeaks possessed leaks, CrowdStrike executives were retroactively claiming that they’d just eliminated hackers from the DNC.
The day after those executive’s claims were published, Guccifer 2.0 appeared, fabricated evidence that seemed (initially) to corroborate what they had claimed about Trump opposition research being targeted with the documents tainted in a manner that supported the specific attribution they had stated.
Mueller’s Indictment

Mueller’s indictment is detailed, contains a lot of facts, and much of it is consistent with the evidence I’ve seen. There is a high level of specificity to it too. However, there are some inaccuracies, some of which conflict with evidence in the public domain. A report citing evidence that I know was sent to Mueller’s office seems to have been selectively disregarded, and when it comes to the topic of Guccifer 2.0, there are very good reasons to have doubts about attribution to a GRU officer.
Putting those issues aside though, the indictment did cite some new details in relation to Guccifer 2.0 and what the persona had apparently done, some of which were completely new revelations to the public. Among the newer details:

This is an interesting correlation, although one would think that they would use a translation site to get the phrases needed and just use them. What would be served by searching for some very specific phrases that they were going to use, but hadn’t yet published? As one Twitter user explains it, this correlation would necessitate supposed GRU officers intentionally creating a clear footprint of their connection to the persona:

It’s difficult to assess Mueller’s claim here, as we have no information from the indictment about the identity of the server that Unit 74455 is alleged to have used, or whether it is or isn’t a part of Elite-VPN infrastructure that we already know Guccifer 2.0 had used.

Unfortunately, it’s difficult to know from the above statement exactly which VPN service is being referenced. We know Guccifer 2.0 used a free, publicly accessible VPN node owned by Elite VPN, but would an overlap of VPN service usage necessarily demonstrate they used the same account there? Is that even the VPN service being referenced here?
It would help a lot if both Twitter and WordPress could release a report on Guccifer 2.0’s usage of Internet infrastructure so that everyone has the full context here.

The indictment also cites Twitter DM communications between Guccifer 2.0 and WikiLeaks, but we don’t get the full context and sentences are cited selectively. Even so, what we do see is interesting.
However, the indictment cites evidence of communications in which WikiLeaks asks Guccifer 2.0 to send him what he had as it would have a much higher impact than what’s he was doing, something they do on June 22nd, a week after he claimed to have already sent all the files.
The obvious question that no one in the legacy press bothered to ask: Why would WikiLeaks say this if the Guccifer 2.0 persona had already sent WikiLeaks what he had?
The indictment also asserts that Guccifer 2.0 only started trying to send content to WikiLeaks towards the end of June and that this failed initially, after which he got some files through to them six days before the DNC leaks were published. Without full context for this allegation, we also can’t be sure whether WikiLeaks was referring to what they already had ready to publish “this week” or whether they were referencing what Guccifer 2.0 had sent them.
GRU Frames Russia & Manufactures Evidence To Support CrowdStrike?

The reasons I still struggle with the indictment arise due to Mueller’s individual attributions to GRU officers, without supporting evidence for said attribution. When combined with evidence that researchers have brought to the surface over the past two years, we are left with a highly improbable scenario regarding Guccifer 2.0’s appearance, at least, under the premise of being a GRU officer:

The GRU attribution, combined with evidence in the public domain, means we are to believe that the GRU essentially tried to frame Russians for hacking the DNC, and even fabricated evidence specifically supporting two critical claims made by CrowdStrike in an article that was published just one day earlier in the Washington Post.
Year-End Conclusion

In summary, evidence indicated that the Guccifer 2.0 persona was operated by someone that wanted to prop up the claims being made by CrowdStrike to the extent that they fabricated evidence and falsified claims in support of statements that had been made by CrowdStrike executives. They wanted to be perceived as Russian and wanted to be attributed to WikiLeaks from the day they emerged.
Guccifer 2.0’s now-exposed objectives do not correlate with the motives of the GRU: they do correlate with the motives that other groups and individuals (based in the United States) would have had at the precise moment in time he appeared.
While I may suspect certain individuals of involvement in this, what I suspect doesn’t matter much. What matters is that the evidence uncovered shows that there is justification for an independent and impartial investigation into the many anomalies of Guccifer 2.0. It also suggests we may not be getting entirely accurate information from the Mueller probe regarding who was really behind the persona.
Clarification on Personal Perspective And Positions Held
I would like to clarify my own position on a few key points, as this writer’s perspective has been relentlessly distorted by others, and I feel it’s important to correct the record on these misconceptions:
- I have not claimed that the DNC was “not hacked at all.” I have explained this and demonstrated a far more nuanced position rather than outright denying any hacking had occurred (I’ve cited FBI agent Adrian Hawkins contacting the DNC about the “Dukes” malware and the discovery of APT-29 malware approximately 6 months later) but am skeptical of the APT-28 malware that appeared while CrowdStrike was at the DNC and contend that the preponderance of evidence in the public domain contradicts the premise of Guccifer 2.0 being a GRU agent.
- I have not claimed that an insider had hacked the DNC, I have merely pointed out that I’ve seen no conclusive evidence that Guccifer 2.0 hacked anything, that his claims have been discredited by ThreatConnect and others and that this may hint at him having obtained the content he released through means other than hacking.
- I have not claimed that the DNC was entirely unhurt by Guccifer 2.0’s actions but have pointed out that Hillary, Podesta, the HRC campaign and the DNC leadership did not have their reputations or credibility damaged by what Guccifer 2.0 released (even though having access to Podesta’s email attachments suggested he had the capacity to do this, he avoided it) and that all the data he shared with GOP aligned individuals related to house races rather than the general election.I’ve demonstrated that this didn’t flip or appear to affect general election voting in those states either!
- I have not claimed that Guccifer 2.0 (or any evidence analyzed in relation to the persona) proves or disproves anything with regards to Seth Rich. Elizabeth Vos and this writer have both repeatedly cautioned from the outset against unduly conflating the two topics, in articles and even an interview. I’ve stated outright that I believe Guccifer 2.0 was lying about Seth Rich and that in making these claims he somewhat contradicts himself.
Wrapping Up 2018

It seems we may now be approaching a point where additional evidence on this topic will only really become available if a formal and impartial investigation into the many anomalies surrounding Guccifer 2.0 is carried out. Besides dragging evidence to the surface, as we have done, there’s not much more we can do to compel such an investigation. Should new developments arise in the form of evidence or establishment media distortions, this author will not hesitate to report on, and where necessary, correct them.
* This article was automatically syndicated and expanded from Disobedient Media.

Leave a comment: